Recap: Fortinet - SASE, SASO, & Beyond

Summary
- This report will be published as a free article on external investment websites. However, we think the content serves as good high-level recap to our recently published research on SD-WAN and SASE and last year's Investor Guide to SASE, in which FTNT heavily features in both.
- FTNT's divergent SASE strategy makes it the most adaptive vendor in the future evolution of networking and network security.
- In fact, we have actually created a variant of SASE, called SASO, to better represent FTNT's ability in converged networking & security. We also believe SASO will gradually subsume SASE over the long-term.
- However, SASE or SASO is just the 'first mile' within the broader networking landscape. We explain FTNT's growth opportunities in the middle and last miles too.
- Relatively, we believe FTNT's valuation looks attractive if investors can see beyond the NTM guidance. Our deeper valuation also suggests ~50% upside.
The SASE and Fortinet Backstory
Since Gartner unveiled SASE (Secure Access Service Edge) in 2019, the concept has dominated networking and network security. Immediately following Gartner’s new concept, vendors from both networking and network security made a beeline to promote themselves as native SASE providers. This was far from the truth, however, because neither the networking players with SD-WAN, like CSCO, nor the cloud-delivered network security players, like ZS, had the full suite of capabilities. Unfortunately, this led to many enterprises being duped, going with who they believed was a holistic SASE provider, only to later discover that numerous third-part integrations were required to make the SASE work, dramatically driving up the TCO.
The early dissatisfaction with SASE was in large part attributed to Gartner’s approach to promoting the concept, which gave vendors the opportunity to mislead, and overall, it created market confusion. When Gartner first released SASE, the publication was very high-level without any specifics nor vendor analysis. Meanwhile, they continued to periodically published their Magic Quadrant (we’ll refer to this as MQ) for WAN Edge Infrastructure, later renamed SD-WAN in 2022, which is the networking side of SASE. However, they waited nearly three years following their initial SASE report before they released a MQ for the security side of SASE in February 2022, named SSE (Secure Service Edge).
Would it not have been simpler to just produce a MQ for SASE? Well, yeah, but its clear that Gartner had internal, potentially political, frictions between the teams and analysts who managed the networking and the network security MQs, preventing the simpler approach.
Since the launch of SASE in 2019, we have been astute in our view that FTNT would become the strongest SASE player. This has been a contrarian viewpoint because for a long while Gartner did not even mention FTNT in its SASE vendor guides/reviews. Gartner’s definition of SASE is entirely cloud-based; that is, heavy-duty networking and security functions should be converged together and conducted off-prem in the nearest PoP (Point of Presence). We have always understood the ‘converged' part, because by removing extensive service chaining, user experience and security effectiveness improve substantially. However, we have never understood Gartner’s insistence on SASE needing to be done in a cloud/edge PoP. Surely, converged networking and security (i.e., SASE), should be conducted wherever is the most economical to do so, and that will depend on the IT environment of the enterprise. Let’s consider two types of IT environment.
- If an enterprise is very cloud-centric, with most applications that employees use being SaaS apps located in the cloud, the enterprise has only a few offices, and a high proportion of remote workers, then doing SASE in the PoP (i.e., Gartner’s definition) makes the most economical sense.
- Though, if the enterprise has a hybrid IT environment, thus operating SaaS in the cloud but also plenty of internal applications in its private data centre, has umpteen branch offices and/or retail outlets, and most employees are office-based, then Gartner’s SASE definition is not ideal.
In the second case, whether or not to do the converged networking/security in the PoP or on-prem, depends on the destination, the proportion of remote workers, and how close a branch office/outlet is to a PoP. In both cases, if traffic is flowing east-west (i.e., internally, e.g., user to user in different branches), ideally the converged networking/security should be done at the branch and then sent along the WAN, removing any need for screening at a PoP. Therefore, in reality, a mix of SASE on-prem and SASE in PoP would be ideal, especially for the second enterprise.
FTNT’s advantage and disadvantage, is that they are the only vendor able to conduct pure converged networking and security on-prem. And we would go as far as saying they are the only vendor able to do pure converged networking and security in the PoP also, though this is debatable. The pros are that FTNT is highly differentiated in the SASE market which is great for competitiveness; the cons are that FTNT is so differentiated that it has somewhat backfired, resulting in Gartner (for a long while) excluding them in SASE evaluations, thus impacting their GTM.
FTNT stands alone here thanks to their custom silicon development, resulting in ASIC chips specially designed for high-intensity compute of networking and security functionalities. The ASICs combined with the in-house hardware and software integration, including their impressive FortiOS operating system, has enabled FTNT to fit every networking (routing, SD-WAN, etc.) and security (NGFW, SWG, ZTNA, etc.) function in a single affordable and compact FortiGate appliance. This dramatically increases performance and decreases costs (compute and management-related costs), compared to conventional on-prem methods of service chaining individual appliances that process a particular function only. To get comparable perf/$, competing vendors can only do so by processing the traffic in their PoP. Thanks to its compactness, the FortiGate is suitable for a range of deployment environments, from large branches, to small branches, and even to home office locations.
In all fairness to Gartner, in the early days of SASE, while FTNT could do the converged networking/security on-prem, they had not yet quite transferred this to a cloud-native form factor leveraging high levels of multitenancy. Though, in our opinion this was still unfair because while FTNT lacked some multitenancy, other vendors Gartner included in their evaluations had really limited scope within SSE, which was not a weakness for FTNT. Nonetheless, since the early days, FTNT has rapidly transferred all of its converged on-prem knowhow to cloud-delivered SASE. Hence, in essence, with FTNT, enterprises can now have their ‘PoP' on-prem or off-prem, and centrally manage their SASE on or off prem too, thanks to the brilliant engineering of the FortiOS. This is why, since 2020, we have been labelling FTNT as the most accommodative SASE player. But not only that, they are the most performant SASE player thanks to their custom silicon + software integration.
In late 2022, our long-held view was somewhat validated when Gartner finally released something substantive and comprehensive on their SASE concept - the Single Vendor Guide to SASE. While this was not a MQ it was a good move by Gartner that helped clear up the market confusion derived via customers trying to reconcile incongruent messages in both the SD-WAN and SSE MQs. Though, with this publication, Gartner was being reactive rather than proactive. Customers had been getting frustrated with the separate evaluations of SD-WAN and SSE. In response, many SD-WAN vendors acquired SSE vendors, and vice versa.
Beginning in 1H22, AVGO set the consolidation wheels in motion to acquire VMware which is now combining Symantec’s SSE and VeloCloud’s (VMware’s earlier acquisition) SD-WAN into a full SASE stack. Then, Netskope acquired SD-WAN vendor Infiot to offer a full in-house SASE platform. In March 2023, HPE acquired Axis Security which will be combined with Silver Peak’s (HPE’s earlier acquisition) SD-WAN to form a full SASE. Then, there is standalone SD-WAN Versa that is developing its own SSE suite to offer full SASE too. The market began consolidating both ways: SSE to SD-WAN and SD-WAN to SSE, as vendors responded to the market needs (and then Gartner responded to the market dynamics).
All along, FTNT has already been that SD-WAN + SSE vendor, or that single SASE vendor. And while a few vendors now can be labelled as single vendor SASE, only FTNT has built their single vendor SASE platform in-house (except for the small acquisition of OPAQ to acquire cloud-delivered ZTNA). The resulting lower technical debt vs. single vendor SASE rivals, will help FTNT continue to innovate at a rapid pace, as it has done over the past several years.
SASE to SASO
During COVID-19, many believed that Gartner’s definition of SASE was the be all and end all for networking and security. However, since then, despite ongoing cloud migrations, it is clear that hybrid IT environments are here to stay. The utilization of the cloud is a must for the majority of organizations, though, due to costs, industry regulations, technical debt, and security concerns, many still need a strong on-prem presence, thus diminishing the idea that cloud-delivered networking/security solutions could fully replace traditional data center infrastructures.
It was also always unlikely that SASE will be the final state because in the world of technology we are constantly shifting from centralized to decentralized architectures, as providers attempt to eke out better performance and greater simplicity. The world has experienced the shift from centralized (e.g., telecom in 1870-1990) to decentralized (e.g., the Internet in 1990s/2000s) back to centralized platforms (e.g., Web 2.0) a number of times in different areas – including cybersecurity. The paradigm shift to SASE is a centralized one, and while it has become very popular, we are already seeing some vendors attempting to improve performance and lower costs by offloading some of the SSE-related compute to user’s device, thus adding in some decentralization.With these thoughts in mind, along with our appreciation for FTNT’s approach to converged networking/security, in 2023 we proposed an alternative to SASE, named SASO, or Secure Access Service Omni. The ‘Omni’ replaces the ‘Edge’ to reflect our view that converged networking/security should be conducted wherever it is most economical and performant to do so – on-prem, in edge PoP, at home office, etc. We believe this more expansive view will gradually prevail and subsume SASE, as hybrid environments persist and we see a continued sway between centralization and decentralization.
To depict our vendor evaluations under the scope of SASO, last year we created the Convequity Impulse, shown below. The two dimensions are Market Adoption (x-axis) and Product Strength (y-axis). Scoring each vendor against these dimensions is based on the present (or May 2023 to be accurate). The horizontal arrow indicates Convequity's assessment for the vendor's future market adoption over the next two years. An arrow pointing to the right indicates an increase in market share over the two-year horizon, and an arrow pointing to the left indicates a decrease in market share over the two-year horizon. The level of current Product Strength has been the main factor in assessing the future market adoption. The other important factor for forecasting future market adoption is the vendor's product roadmap. This is an important factor because there are many vendors in which we've scored lower on current Product Strength, but it's not the case that they will experience poor market adoption if they have a strong product roadmap. We discuss at length the rationale behind each vendor’s positioning on the Convequity Impulse in our multi-part Investor Guide to SASE and SD-WAN & SASE Industry Review exclusive for Convequity subscribers, and we will shortly be reviewing the Convequity Impulse for 2024.
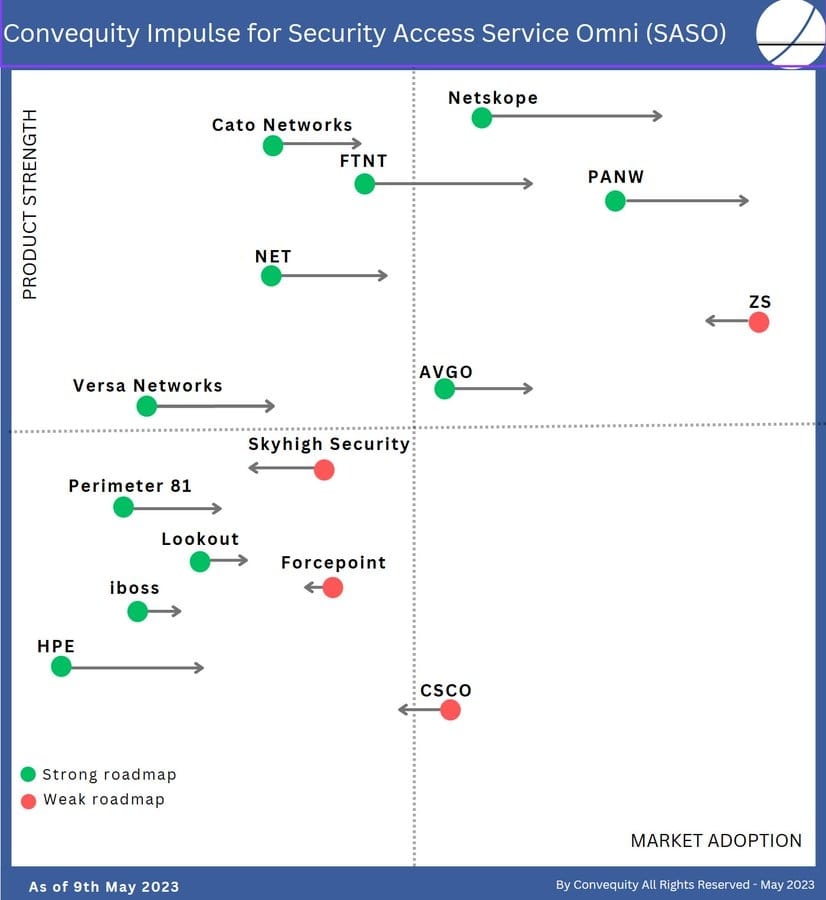
Beyond SASE & SASO – the evolution of secure networking
SASE is currently the focal point of networking and security transformation, though in reality it is only one part of the bigger picture. Inspired by Dell’Oro, we view the whole networking/security landscape as the first mile, the middle mile, and the last mile, which are common references to the different transit stages of data packets.
The first mile is also known as the WAN Edge, and is where SASE operates. Essentially, it is the distance from the user and their device to the point of converged networking and security processing. As explained, under the common understanding of SASE, this means the distance between the user and the PoP. Though, under SASO, this would be the distance between the user and either the PoP or the on-prem gateway that processes the SD-WAN and SSE, if the enterprise has FTNT deployed, for example. Though this first mile is only a portion of the journey that a data packet needs to take to reach its destination – whether that be in the cloud or even in a private data centre (if an enterprise or SMB has insufficient MPLS and/or the user is in a remote branch or is a WFH worker, then the packet may go through SASE even to get to the private data centre).
Once the packet has been processed in a PoP (for ease let’s now refer to PoP as meaning either edge PoP or on-prem PoP, under the SASO terminology), it needs to traverse the middle mile which consists of numerous hops through numerous interlinked networks and the Internet.
Once the packet has made it through the middle mile, it must embark on the last mile. The last mile is where the packet reaches its destination, ramping onto the cloud to connect with a SaaS application, or heading to the data centre to reach an internal application. Currently, while we are seeing some consolidation among a few vendors for the first mile, enterprises use a multitude of different providers for the middle and last miles. So, gradually and over time, we expect the market to want a degree of consolidation across the three stages, because otherwise an enterprise’s highly performant first mile will be diluted by inefficiencies in the middle and last miles, rendering the pursuit for better user experience futile.
We view FTNT as being well-positioned to take advantage of this likely consolidation across first, middle, and last mile, though it will be a decade-long investment thesis for it to play out, mainly because networking is very slow-moving. In the following sections we will discuss FTNT’s strengths amid each of the transit stages.
The First Mile
In essence the first mile is SASE or SASO, so we know why FTNT has a competitive advantage here. They are by far the most accommodative player thanks to being able to process converged networking/security either on-prem via the FortiGate or in an edge PoP via their FortiSASE. Furthermore, FTNT provides true convergence, whereas most other vendors need some amount of service chaining due to them not having native SD-WAN or native SSE, and/or because, unlike FTNT, they haven’t built the convergence from the ground up, but achieved it via bolt-on methods.
At present, FTNT is behind the likes of ZS and PANW in terms of SASE market share, and this is partly why FTNT has been trading at lower multiples even before the company dropped its NTM growth by a wide margin. Though, for us, a key component of the alpha is that FTNT has by far the largest customer base of all network security, thanks to its pervasive deployment of its ASIC-powered FortiGate – about 700k customers. All these customers are using FortiOS (the majority on the GA current version; a few on the newest version for testing; FTNT also maintains an older version for backup support in which a small portion of customers are using at any given time), and this is what enabled FTNT to basically give SD-WAN to most of these customers initially for free - they just updated FortiOS with SD-WAN provisioned and instantly acquired a massive SD-WAN installed base. It seems as though the same playbook will be executed for SASE, though with more of a focus on monetization from the outset. When we think about the lengthy and arduous deployments for ZS’ or even PANW’s SASE, this is a huge competitive advantage for FTNT.
The Middle Mile
At present, FTNT is far behind being a leader in the middle mile. The top SASE names in this middle mile domain are NET, AKAM, and Netskope, who have carefully crafted, and globally dense, peering networks. NET and AKAM run the largest CDN networks, which makes them a natural leader in the middle mile. Though non-SASE names are also relevant here, such as EQIX who provides the building and power for colocation data centre customers, but also provides network connectivity between PoPs, and Graphiant, who provides NaaS, or Networking-as-a-Service. Such players have very dense globally distributed PoP networks, ideal for the middle mile.FTNT has huge ambitions here. The long-term goal is to have > 100 PoPs that they own, which is very divergent because other dense PoP network players, like NET, ZS, and Netskope, use colocation facilities from EQIX, meaning they don’t actually own the PoP/data centre. FTNT’s differentiated PoP strategy, while capex heavy, over the long-term will be less restrictive and enable FTNT’s capable engineering teams to architect their ASIC stack in the most optimal way.
However, the SASE market is not going to wait for FTNT to build ~100 of its own PoPs, therefore, as a temporary measure FTNT has been using Google’s Cloud network to rapidly expand its PoP presence. This part of FTNT’s strategy is the same as PANW’s entire SASE strategy. FTNT will run FortiOS in VM or container form factor on Google's hardware. This will help FTNT close the SASE coverage gap but is really a temporary strategy. By not having their own ASICs running in their PoPs, COGS will increase and put pressure on gross margin. This is why, additionally, FTNT is leveraging EQIX's services to expand its PoP presence, which is a slower expansion but ensures they can use their ASICs. Nonetheless, using Google has enabled FTNT to aggressively expand to a total of over 100 PoPs and compete with those with denser global networks such as NET, ZS, and Netskope.
Here, we have described a three-pronged approach (proprietary PoPs, Google PoPs, and EQIX colocation PoPs) for FTNT building out the SASE coverage, and as a result, also build out a strong middle mile presence. However, really FTNT’s strategy is four-pronged because they are also executing another colocation strategy by co-building a number of PoPs with service providers (SPs), whereby the SPs use FTNT's ASICs and FortiOS to run their own private SASE for their customers.
This fourth prong is an interesting and potentially very fruitful strategy because SPs, like ISPs, are competing on price, and therefore they may want SASE but going with ZS or PANW would not be viable because of the vendors’ price, which includes the colo provider’s or hyperscaler’s gross margin plus ZS/PANW’s gross margin. By opting to run FTNT’s SASE, SPs will save substantial costs by avoiding the typical colo gross margin and because FTNT is just providing the silicon, the infra, and the software for SASE, it isn’t managing the SASE, meaning it can charge far less than ZS and PANW and garner great appeal from the SPs. This is a really underserved segment of SASE and one in which FTNT has shaped a specific strategy to capitalize on.
Collectively, this four-pronged strategy will eventually make FTNT a promising player in the NaaS market, an emerging SaaS domain suitable for organizations that want to reduce their networking capex and management costs, and instead leverage an opex-based networking paradigm.
With this four-pronged PoP coverage approach, in the short-term (or already), FTNT has a fairly solid middle mile presence in which to deliver further network performance gains for enterprise customers. They also have dramatically increased their first mile coverage by having more PoPs around the globe. Though, the most value-creating aspect will occur over the long-term, when FTNT has a significant portion of its PoPs, proprietarily engineered, and running on its ASICs. As we have discussed in detail in our subscriber content, such vertical integration, from the software layer, to the infra layer, down to the silicon layer, is extremely gross margin and FCF margin accretive. With that, we think its possible FTNT’s terminal FCF margin can increase to ~45% vs. the current LTM FCF margin of 32%.
The caveat as FTNT builds its middle mile presence, however, is that it requires rare talent to be able to architect a BoB next-gen global network, such as NET's and Netskope's. While FTNT has top talent in abundance, building a global network is far removed from its engineering feats to date. Hence, there is a non-negligible possibility that they fail to reach the potential.
The Last Mile
The last mile, also referred to as the application edge, is the stage of the journey where the data packet connects with the application, which could be in the cloud or on-prem. FTNT is very strong in the on-prem application edge, as they have a full stack dedicated to application performance acceleration and protection. For instance, they have FortiADC for application acceleration, availability, load balancing, and security. They also have FortiWeb, which is their web application firewall with built in API protection, and a number of other solutions, like DDoS and bot protection, to keep applications safe from attack, and even great email security. You can even count the FortiGate in the last mile segment, because they do the screening of incoming traffic too. In regards to the application edge in the cloud, FTNT is less known but still pretty strong, as they have FortiWeb in SaaS form factor, and have VM-based cloud firewalls that are easy to provision in the cloud.
Summing Up
While SASE is the predominant focus right now, investors should note it will evolve and will likely be subsumed into a broader purchasing landscape. Thinking of this broader landscape via first, middle, and last miles, is a useful reference framework for assessing the competitive environment.
FTNT is very solid in the first and last mile. In the first mile (aka SASE), we would say FTNT’s PMF (Product Market Fit) is perfect but its GTM has been lacklustre to date. Though, this is likely to change as FTNT replays its SD-WAN playbook to its 700k installed base. The last mile is where FTNT is most mature and established, albeit less so in the cloud application edge. And the middle mile is where most long-term incremental value will arise, as once FTNT has a dense global PoP network driven mostly by its ASICs, it will be able to provide BoB NaaS, which is a promising trend still in the early days, and increase gross margins while remaining its competitiveness thanks to its vertical integration.
The middle mile segment is currently very fragmented and regionalized, except for a few global names. We expect FTNT to benefit from the value created by this segment being consolidated.
If, as we predict, FTNT can be a winner in the first, the middle, and the last mile, the company will be arguably the most pervasive networking and security name, and as we journey to this future point in time, sizeable shareholder value should be created.
Valuation Considerations
It is not surprising to see poor valuation metrics for FTNT at present. FY24 growth guidance has plummeted as FTNT feels the aftermath of the supply chain congestion driven demand during 2021/22, which accelerated product growth to ~40% for a few quarters. Resultingly, many customers are already well supplied with FortiGates, leading to sharp growth deceleration throughout 2023 and going into 2024. The valuation metrics shown below merely factor in the present or NTM view, without taking account of FTNT's very durable growth, catalyzed by the first, middle, and last mile tailwinds aforementioned.
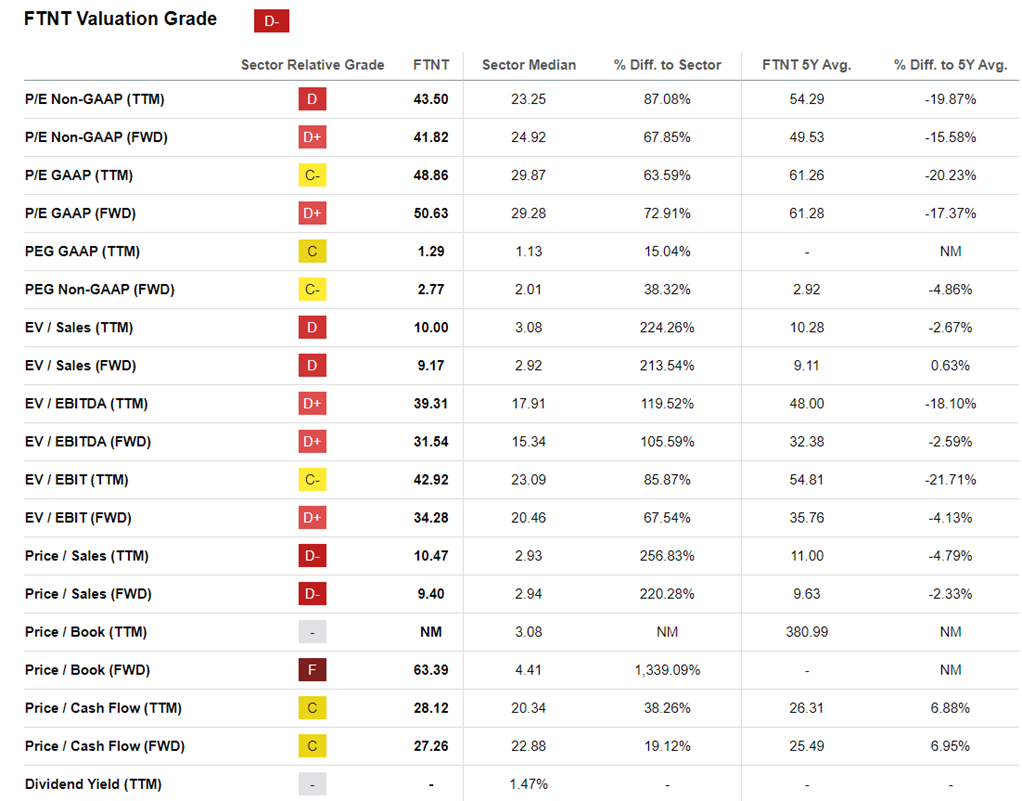
We prefer to look at the EV/(FCF-SBC) multiple and compare this with the Rule of 40 (inc. SBC). When applying this relative valuation FTNT looks attractive with a EV/(FCF-SBC) of 35x and a Rule of 40 (inc. SBC) of 37 (note, we calculate the Rule of 40 with NTM growth and LTM FCF margin and SBC %). Compare this to PANW with a Rule of 40 of 40 and an EV/(FCF-SBC) of 50x, and CRWD with a Rule of 40 of 41 and an EV/(FCF-SBC) of 216x, and you can see FTNT's attractiveness.
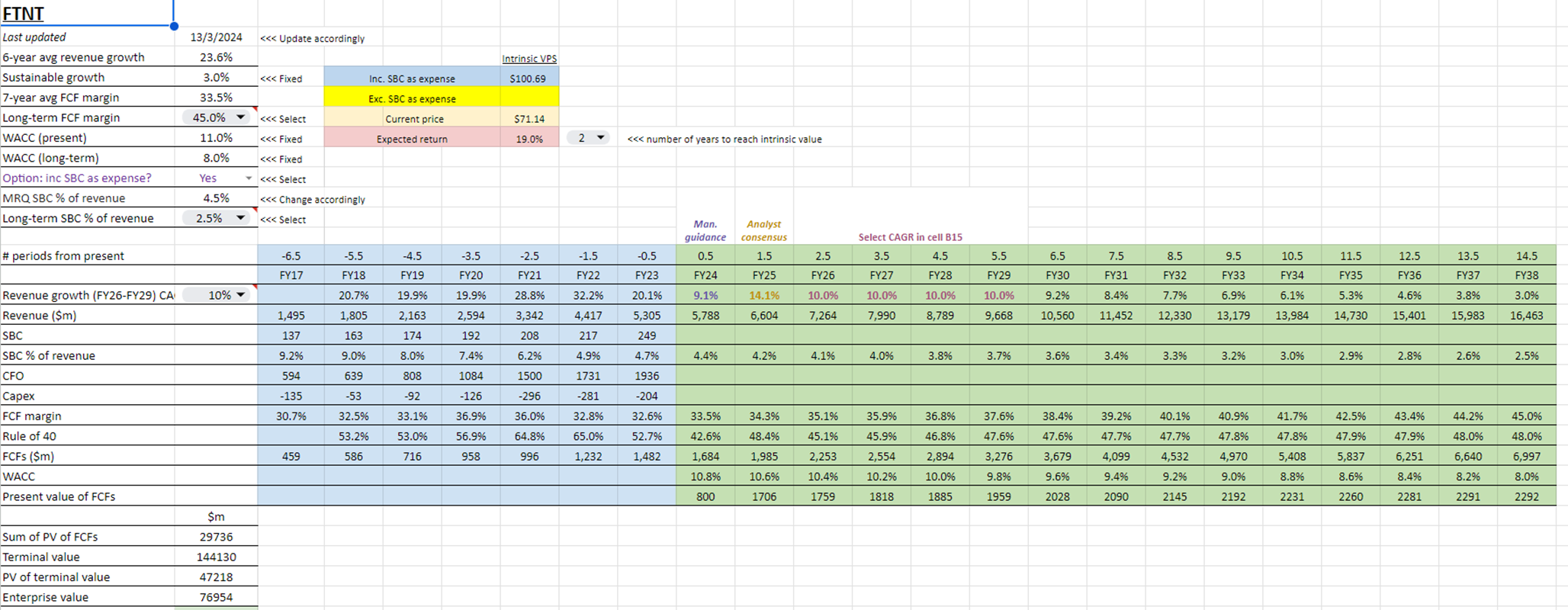
However, for companies with such a long-term durable growth outlook, it makes more sense to put more weight on a DCF valuation. Here is a snippet of our DCF valuation model for FTNT. The settings shown are for the base case: a 45% terminal FCF margin, a 10% CAGR for FY26-FY29 following the guidance/consensus forecasts for FY24 and FY25, and a terminal SBC % of 2.5%. Click the link to view the full model, showing the reconciliation from enterprise value to equity value and value per share. As can be seen, our base case suggests a ~50% upside for FTNT from the current price.
Conclusion
After many years of being dismissed by Gartner, FTNT is now quickly gaining recognition for its divergent SASE approach, and is now benefitting from the single vendor SASE trend. We will be doing our official Convequity Impulse review shortly, though for us it looks like FTNT is showing increasing strength and finally delivering to our long-held expectations within the SASE domain. Though SASE or SASO is just one growth avenue. The middle mile, where FTNT can provide NaaS, is another promising growth catalyst that is not being considered by investors whatsoever.
On top of the growth prospects beyond SASE, FTNT has great momentum in OT/IoT security, another area of FTNT's business in which we have extended content, though we'll save that for another article. In terms of valuation, we think FTNT is trading relatively undervalued when considering its excellent financials and business performance, conveyed via the Rule of 40. And our base case DCF supports this view also.




